
5-Point Likert Scale
Is 5-Point Likert Scale a Better Choice to use? SHARE THE ARTICLE ON Table of Contents Before learning more about the Likert scale, let us
Find the best survey software for you!
(Along with a checklist to compare platforms)
Take a peek at our powerful survey features to design surveys that scale discoveries.
Explore Voxco
Need to map Voxco’s features & offerings? We can help!
Find the best customer experience platform
Uncover customer pain points, analyze feedback and run successful CX programs with the best CX platform for your team.

We’ve been avid users of the Voxco platform now for over 20 years. It gives us the flexibility to routinely enhance our survey toolkit and provides our clients with a more robust dataset and story to tell their clients.
Steve Male
VP Innovation & Strategic Partnerships, The Logit Group
Explore Regional Offices

Find the best survey software for you!
(Along with a checklist to compare platforms)
Take a peek at our powerful survey features to design surveys that scale discoveries.
Explore Voxco
Need to map Voxco’s features & offerings? We can help!
Find the best customer experience platform
Uncover customer pain points, analyze feedback and run successful CX programs with the best CX platform for your team.

We’ve been avid users of the Voxco platform now for over 20 years. It gives us the flexibility to routinely enhance our survey toolkit and provides our clients with a more robust dataset and story to tell their clients.
Steve Male
VP Innovation & Strategic Partnerships, The Logit Group
Explore Regional Offices

Find the best survey software for you!
(Along with a checklist to compare platforms)
Take a peek at our powerful survey features to design surveys that scale discoveries.
Explore Voxco
Need to map Voxco’s features & offerings? We can help!
Find the best customer experience platform
Uncover customer pain points, analyze feedback and run successful CX programs with the best CX platform for your team.

We’ve been avid users of the Voxco platform now for over 20 years. It gives us the flexibility to routinely enhance our survey toolkit and provides our clients with a more robust dataset and story to tell their clients.
Steve Male
VP Innovation & Strategic Partnerships, The Logit Group
Explore Regional Offices
Any business that wants to succeed and grow must practise effective risk management. Risk management usually involves locating, evaluating, and controlling risks that could have a detrimental effect on a company’s operations, finances, reputation, and other crucial areas. Businesses can foresee and prepare for potential risks courtesy to a clearly defined risk management approach, which lowers the chance and severity of unfavourable effects.
But nonetheless, risk management may be a challenging and time-consuming procedure that calls for knowledge and resources. We’ll go over the five key steps in a risk management process in this blog, and will also touch upon how AI-driven risk management platforms can simplify and economise this process. Understanding and implementing a risk management approach can help you safeguard your company and achieve long-term success, whether you run a modest startup or a major multinational. Let’s get into it!
Proactively identify risk and avoid financial losses with Voxco Intelligence’s powerful risk management platform
These are the 5 key steps that create an effective risk management process:
Let’s delve into each step in detail.
Identifying potential risks that could affect your organization is the first stage in the risk management process. This essentially involves conducting a thorough analysis of your company’s operations, environment, and business procedures to find any potential risk factors.
Let’s examine two popular methods for identifying risk:
1. SWOT Analysis
Doing a SWOT analysis is one practical way to find threats. SWOT is an acronym that stands for Strengths, Weaknesses, Opportunities, and Threats. Businesses can use this analysis to pinpoint their internal and external opportunities and threats as well as their strengths and weaknesses. Businesses should take proactive steps to reduce risks by recognising potential threats before they materialise into significant issues.
2. Brainstorming:
Brainstorming is another useful method for detecting risks. Using a brainstorming process will help you come up with a variety of ideas to spot hidden risks. Businesses can acquire insightful perspectives and useful insights on potential hazards by including a variety of stakeholders in the brainstorming process.
Financial risks, operational risks, strategic risks, regulatory risks, and reputational risks are a few notable risks that firms may encounter:
Click here to learn about how businesses can also leverage AI-driven platforms to identify risk.
Businesses can take proactive steps to limit risks by accurately detecting possible threats before they cause serious harm. We’ll delve into risk analysis, the second step in the risk management process, in the next section.
The second phase in the risk management process is to examine potential risks that have been discovered in the previous step. This entails evaluating the possibility and consequences of each stated risk.
Quantitative analysis and qualitative analysis are the two main techniques used to carry out risk analysis.
In order to handle and minimise risks, it is essential to understand their likelihood and impact. Companies must evaluate a risk’s potential consequences to decide whether or not it is acceptable. For instance, the business may take a financial risk if it has a significant impact but a low likelihood of happening. A reputational risk, on the other hand, can have a lower consequence but a higher likelihood of happening, making it unacceptable to the organisation.
Companies must also take into account the potential costs associated with risk mitigation. Weighing the costs of risk mitigation methods against the advantages of lowering a risk’s likelihood or impact is crucial because these strategies can be expensive.
Businesses can analyse risks and make well-informed decisions about how to manage them. In the next section, we’ll explore the phase in the risk management process – risk evaluation.
Risk evaluation is the third step in the risk management process. In this step, risks are prioritised according to their potential impact after being assessed for severity and likelihood. Businesses can identify the risks that offer the most threat and demand the most attention by evaluating the risks.
Risk Evaluation Techniques:
Businesses can assess risks using a number of techniques, such as a risk matrix and risk scoring.
Risk Prioritization
After risks have been assessed, it’s essential to rank them according to their potential impact. This allows organisations to focus their resources on resolving the most major risks first. Prioritization should always be determined by a combination of likelihood and severity, with risks that are both likely and highly impactful, or severe, being addressed first. Furthermore, businesses should keep in mind the resources available to handle each risk and the possible negative effects of doing nothing.
A crucial phase in the risk management process is risk evaluation, which enables firms to pinpoint the issues that need the most attention and resources. Businesses can make sure that they concentrate on resolving the risks that pose the biggest harm to their operations by prioritising risks. This can lessen the likelihood that risks will negatively affect the company and increase the overall efficacy of the risk management strategy.
Businesses can assess risks more effectively by implementing an AI-driven fraud and risk management platform. By considering a range of variables, including historical data and market patterns, such platforms can automatically identify and evaluate risks. As new risks are discovered, the system will deliver real-time notifications, enabling businesses to react swiftly and successfully.
Addressing risks is the subsequent phase in the risk management process once they’ve been identified, examined, and evaluated. By treating risks, businesses implement controls to reduce the likelihood and the impact of these risks. Risk treatment approaches include risk avoidance, risk transfer, and risk mitigation.
It’s crucial to keep in mind that managing risks requires ongoing effort. To make sure controls are working properly, they must be regularly monitored and modified as needed. In addition, it’s crucial to order the adoption of controls according to how serious and likely the hazards are.
The risk treatment process can be made more efficient by implementing an AI-driven fraud and risk management platform. The platform can automatically detect and rank risks, provide suitable controls based on best practises, and track the efficiency of controls that have been put in place.
Monitoring and reviewing risks is the last phase in the risk management process. This step involves analysing the risk management process to find opportunities for improvement and regularly assessing the effectiveness of controls. Monitoring and reviewing risks helps businesses ensure that the risk management process they have put in place remains effective and up-to-date.
1. Monitoring Risks
This step entails monitoring the performance of implemented controls and spotting any potential new risks. It’s crucial to have a system in place for tracking risks and to establish regular checkpoints for evaluating the efficacy of controls. This enables companies to immediately identify any problems and, if necessary, install new measures.
2. Reviewing the Risk Management Process
This stage entails evaluating the entire risk management procedure to find areas that could potentially be improved. To keep their risk management procedures current and efficient, businesses should evaluate them frequently. This may entail examining policies and processes, locating potential control weak spots, and revising risk assessments in light of new data.
Businesses can ensure they’re equipped to handle any potential issues by regularly monitoring and reviewing risks. This stage is particularly crucial in the continuously evolving corporate world of today, where new risks might appear suddenly and without warning.
Experience the power of AI with Voxco Intelligence.
Receive real-time insights that drive impact within your organization.
Any effective business strategy must include the risk management process. Businesses can proactively address various risks and minimize their impact by identifying, analysing, evaluating, treating, and monitoring risks.
To sum up, organisations that prioritise the risk management process and use technology to improve their operations are better able to handle potential risks and seize chances for expansion and success. Businesses can enhance their overall risk management capabilities and position themselves for long-term success by adhering to the five important steps indicated in this article and by using the right AI-driven fraud and risk management platform.
1. What is a risk management process?
A risk management process in a 5 step framework that helps businesses identify, manage, and eliminate potential risks before they negatively impact the organization.
2. What are the 5 risk management process?
There are 5 key steps in the risk management process, namely:
3. Why is the objective of risk management?
The objective of risk management is to identify and prevent potential risks before they negatively impact an organization.
Join the network of 500+ happy survey creators.
Explore all the survey question types
possible on Voxco
Read more

Is 5-Point Likert Scale a Better Choice to use? SHARE THE ARTICLE ON Table of Contents Before learning more about the Likert scale, let us
Data Lake Vs Data Warehouse – What’s the Biggest Difference? SHARE THE ARTICLE ON Table of Contents What’s the biggest difference between a data lake

The 5 Key Steps in an Effective Risk Management Process SHARE THE ARTICLE ON Table of Contents Introduction Any business that wants to succeed and
Auto Dialer vs Predictive Dialer: Know the Difference SHARE THE ARTICLE ON Table of Contents The average benchmark for First Call Resolution is 70%. This
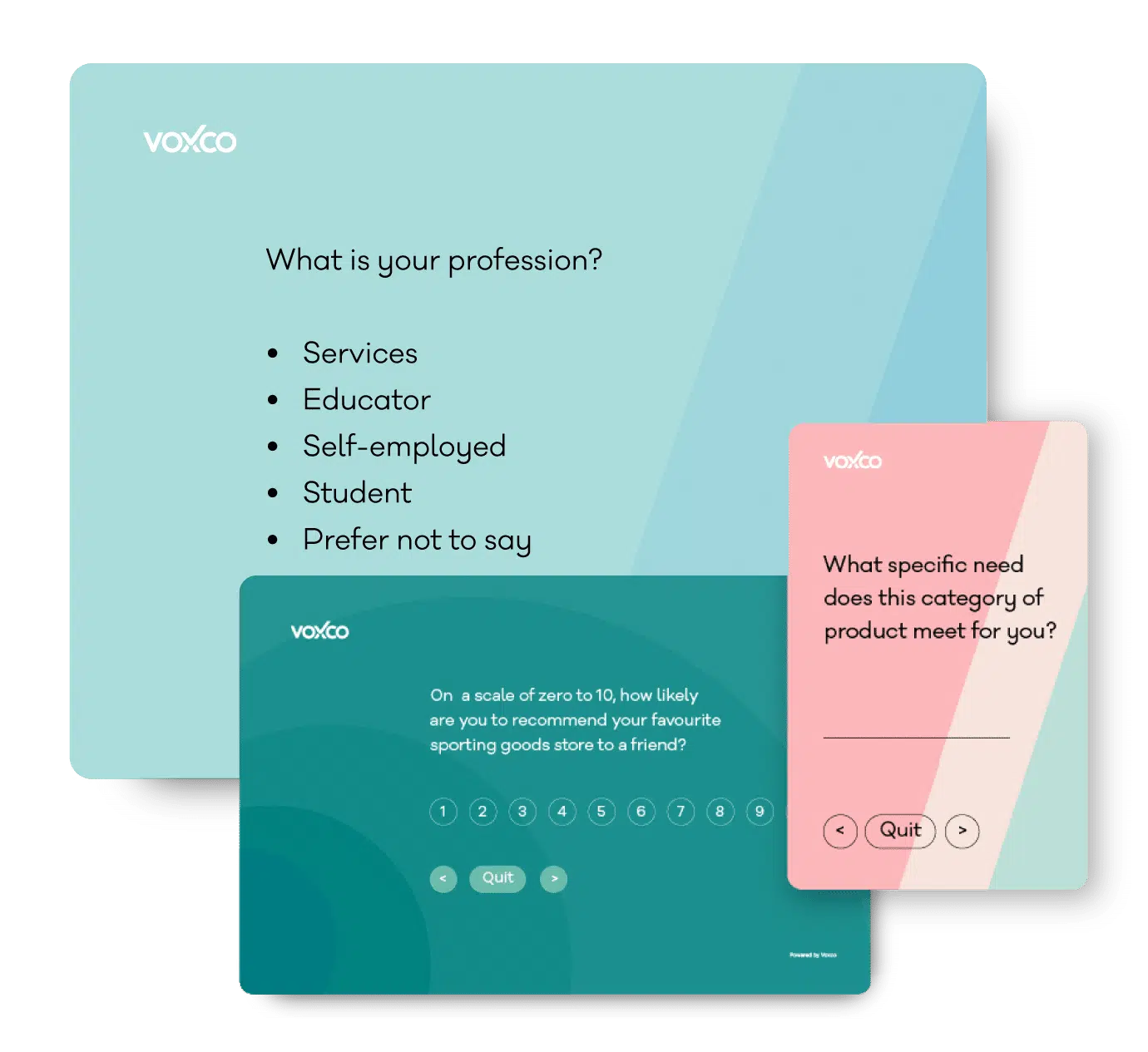
Survey Features Single answer survey question Build engaging surveys with Image area evaluator survey questions! Get a free evaluation Unlock your Sample Survey Get your
Target Market Voxco is trusted by 450+ Global Brands in 40+ countries See what question types are possible with a sample survey! Try a Sample
We use cookies in our website to give you the best browsing experience and to tailor advertising. By continuing to use our website, you give us consent to the use of cookies. Read More
| Name | Domain | Purpose | Expiry | Type |
|---|---|---|---|---|
| hubspotutk | www.voxco.com | HubSpot functional cookie. | 1 year | HTTP |
| lhc_dir_locale | amplifyreach.com | --- | 52 years | --- |
| lhc_dirclass | amplifyreach.com | --- | 52 years | --- |
| Name | Domain | Purpose | Expiry | Type |
|---|---|---|---|---|
| _fbp | www.voxco.com | Facebook Pixel advertising first-party cookie | 3 months | HTTP |
| __hstc | www.voxco.com | Hubspot marketing platform cookie. | 1 year | HTTP |
| __hssrc | www.voxco.com | Hubspot marketing platform cookie. | 52 years | HTTP |
| __hssc | www.voxco.com | Hubspot marketing platform cookie. | Session | HTTP |
| Name | Domain | Purpose | Expiry | Type |
|---|---|---|---|---|
| _gid | www.voxco.com | Google Universal Analytics short-time unique user tracking identifier. | 1 days | HTTP |
| MUID | bing.com | Microsoft User Identifier tracking cookie used by Bing Ads. | 1 year | HTTP |
| MR | bat.bing.com | Microsoft User Identifier tracking cookie used by Bing Ads. | 7 days | HTTP |
| IDE | doubleclick.net | Google advertising cookie used for user tracking and ad targeting purposes. | 2 years | HTTP |
| _vwo_uuid_v2 | www.voxco.com | Generic Visual Website Optimizer (VWO) user tracking cookie. | 1 year | HTTP |
| _vis_opt_s | www.voxco.com | Generic Visual Website Optimizer (VWO) user tracking cookie that detects if the user is new or returning to a particular campaign. | 3 months | HTTP |
| _vis_opt_test_cookie | www.voxco.com | A session (temporary) cookie used by Generic Visual Website Optimizer (VWO) to detect if the cookies are enabled on the browser of the user or not. | 52 years | HTTP |
| _ga | www.voxco.com | Google Universal Analytics long-time unique user tracking identifier. | 2 years | HTTP |
| _uetsid | www.voxco.com | Microsoft Bing Ads Universal Event Tracking (UET) tracking cookie. | 1 days | HTTP |
| vuid | vimeo.com | Vimeo tracking cookie | 2 years | HTTP |
| Name | Domain | Purpose | Expiry | Type |
|---|---|---|---|---|
| __cf_bm | hubspot.com | Generic CloudFlare functional cookie. | Session | HTTP |
| Name | Domain | Purpose | Expiry | Type |
|---|---|---|---|---|
| _gcl_au | www.voxco.com | --- | 3 months | --- |
| _gat_gtag_UA_3262734_1 | www.voxco.com | --- | Session | --- |
| _clck | www.voxco.com | --- | 1 year | --- |
| _ga_HNFQQ528PZ | www.voxco.com | --- | 2 years | --- |
| _clsk | www.voxco.com | --- | 1 days | --- |
| visitor_id18452 | pardot.com | --- | 10 years | --- |
| visitor_id18452-hash | pardot.com | --- | 10 years | --- |
| lpv18452 | pi.pardot.com | --- | Session | --- |
| lhc_per | www.voxco.com | --- | 6 months | --- |
| _uetvid | www.voxco.com | --- | 1 year | --- |